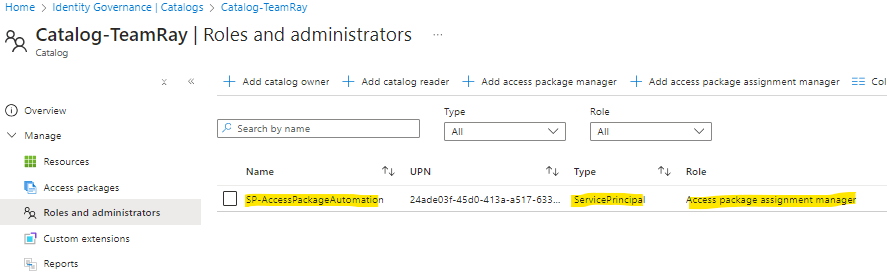
Microsoft released new versions (2.4.xx.0) of Microsoft Entra Connect Sync last month – October 2024, and advising all customers are required to upgrade to the minimum versions by April 7, 2025.
The expected impacts from not upgrading are as follows:
- Configuration of AD FS scenarios through the Connect Sync wizard may not work
- Configuration of PingFederate scenarios through the Connect Sync wizard may not work
So if you are configuring AD FS or using PingFederate – this looks like something to look into.
Upgrading Entra Connect (won’t auto upgrade!)
The minimum versions required to avoid the impact are as follows:
- Customers in commercial clouds: 2.4.18.0 or higher.
- Customers in non-commercial clouds: 2.4.21.0 or higher.
If you are a customer in non-commercial clouds, 2.4.18.0 won’t do as it looks like 2.4.21.0 contains a bug fix specifically for non-commercial clouds.
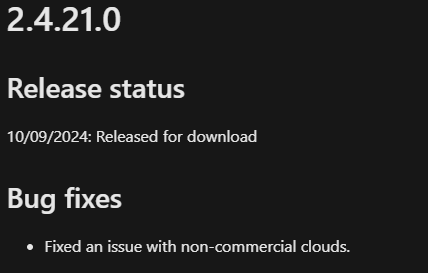
The documentation mentions the below on the automatic upgrade, however I do not find this to be accurate for these two specific versions.

When you check the ‘Release status’ of versions 2.4.21.0 and 2.4.18.0 on Microsoft Entra Connect version history, you will find that these two versions have been ‘Released for download’, rather than ‘Released for download and autoupgrade’.
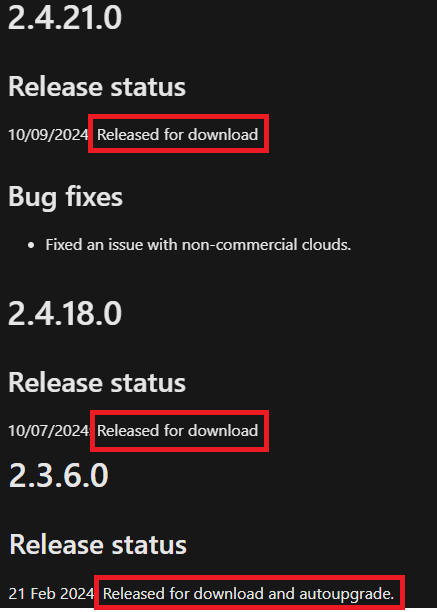
Hence I believe a manual download and upgrade will need to be performed, and prior to upgrading, you will also need to ensure you meet the below minimum requirements for the versions:
- .NET 4.7.2
- TLS 1.2
Conclusion
I’ve since then committed a change to the documentation Hardening update to Microsoft Entra Connect Sync AD FS and PingFederate configuration.
You can also consider moving to Microsoft Entra Cloud instead of Entra Connect Sync as mentioned in the documentation. A good comparison between Entra Connect and cloud sync is available on What is Microsoft Entra Cloud Sync?.
If your organisation configures AD FS or PingFederate via Entra Connect – why not act now?